As you probably know, the cyber threat is constantly growing. I was just watching this morning about how school systems are being attacked and that the issues that they’re running into are so pervasive. All organizations are under the persistent threat of having their data compromised.
In this post, I hope to demonstrate how you can identify what kind of information that your firm might handle, what kind of responsibilities you might have for information, and then also, how do you address those responsibilities with policies and procedures?
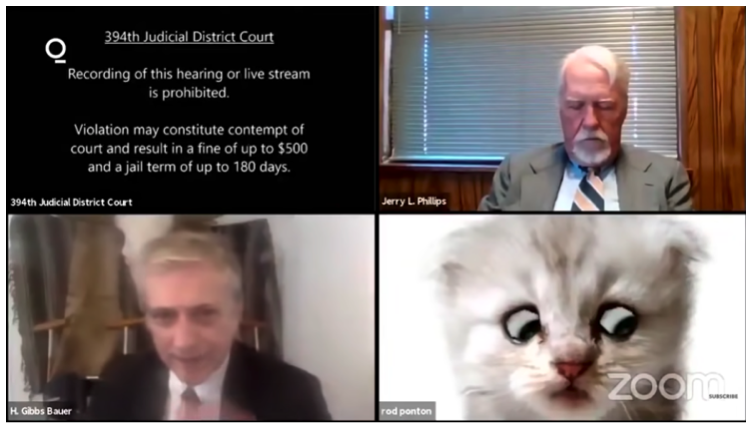
I want to start out with something everyone has probably seen, the “I’m not a cat video”, you know it was a zoom court.
When I saw Rod Ponton, a county attorney in Presidio County, Texas, unable to figure out how to turn off the cat filter on his Zoom call during a court hearing, I laughed.
While we may chuckle about it, and the judge said “Everyone involved handled it with dignity, and the filtered lawyer showed incredible grace. True professionalism all around!”, I think there are some serious takeaways.
It was reported that Mr. Ponton’s computer had a problem, so he used an assistant’s computer for the zoom session. The assistant’s daughter had previously used the same computer and had installed a Snap Camera cat filter.
Lawyers and other professionals have a responsibility to keep specific information about the clients private. If that computer is used by the assistant while doing work for Mr Ponton, then that computer may have client data both in local files and remotely accessible files.
Making private client information accessible to direct viewing be the assistant’s family member is s a mild risk, but by allowing the download and installation of unvetted software can lead to malicious exfiltration of that private information. Putting Mr. Ponton and his firm at risk of PCI, HIPAA or other costly violations.
How do we know? How do you keep your firm safe from this kind of exposure?
In this post, I will address; How do we analyze where we’re at? And what we need to do?
We need a plan. Cyber security can be really overwhelming for everyone. We want to limit the scope, but we need to identify where vulnerabilities lurk.
We want to set some rules and we want to enforce and be able to enforce and monitor those rules.
This plan is derived from a number of different frameworks. I’ll talk about what a Framework is later in this post.
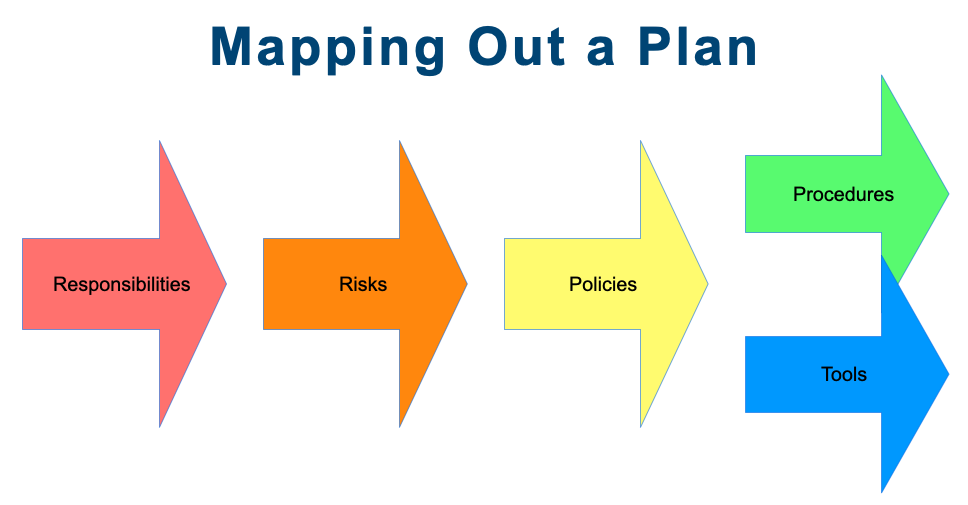
The first thing is responsibilities, you want to identify what are you responsible for, what kind of information, where is it held and used, etc.
Once you can list you’re responsibilities, then you identify the risks related to those responsibilities.
Then based on that, create some policies, some rules that you’re going to follow that will help you mitigate those risks.
Procedures will help follow those policies and tools that will also help you ensure that things are being done, so you’ll use the tools within the procedures so they kind of go hand in hand.
Once you start to break it out this way, then it becomes manageable, manageable, and that’s where kind of we’re going to go.
You want to identify what kind of data you’re working with?
What information are you collecting?
Someone fills out a form an intake form and they become a client.
Some personal identifying information, payment information, business information.
Think about why you’re collecting it and how it’s being used. Then also think about how sensitive that is.
This is essentially an information audit and it provides a profile of the kind of data that you’re keeping.
Is it, you know, just like I said PII, which is Personal identity identifying information.
Is it payment information which is falls under PCI?
Is it health information which would invoke HIPAA?
Is it company confidential information like patent information or trademark registrations or product development plans?
Once you know kind of your responsibilities, you can work on a framework and yeah, it may actually work under a couple of different frameworks.
NIST, I’ll get into a little bit more detail in the next slide as well as PCI.
NIST is National Institute of Standards and Technology, and it’s a government agency and they created a cyber security framework, which is an overarching concept which a lot of other frameworks incorporate.
Almost always, every business will begin with the NIST framework. If you’re doing sales or ecommerce the add the PCI DSS requirements. Depending on how your business runs, maybe the whole business falls under that and the others then become very specific: HIPAA, NERC CIP, …
The Cybersecurity Maturity Model Certification extends DFARS CDI for anyone who is a supplier of services to the US government. Depending on the type of supplier, there are different levels that that you’ll have to meet.
The NIST CSF is a ring because it’s a continuous improvement cycle. Let’s start with something basic like your desktop computer or your laptop.
You’ve identified that you’re going to PROTECT it, so you want some endpoint protection on it, which is essentially antivirus / antimalware.
Once you’re protecting it, then you will to move to DETECT. Which is knowing an attack is underway. Rapid Detection and Response (RDR), which is a feature of some of the advanced endpoint protection products. They detect that malware is actually starting to run on the system. By looking at the profile of the applications that you run, it can identify that something abnormal is happening. It will provide a warning if for example, an application trying to access a system file it does not normally access.
The next step is to RESPOND. Where decide what you want to do about the potential attack? Do you want to isolate the computer? Do you want to try to stop that application from running? You’ll see a number of different things that some of the advanced protections do.
The last step is to RECOVER. Yes, you’ve stopped the attack, but was any data compromised or damaged? How do you get it back up into the normal running state.
From there you start the cycle over. You identified something new, for example email or your network, and start with how do you Protect it?
You’re constantly improving by running through that cycle using that framework.
Another framework is the payment card industry. They’ve created a security standard, PCI-DSS. You’re not legally obligated to follow it, but if you do any dealings with the bank, they will require you to certify for it. You could lose your ability to collect credit card payments if you don’t. If your credit card usage is minimal, you may be able to self-certify. If you have a significant number of transactions or have your own applications or network, then you may need to use a Qualified Assessor.
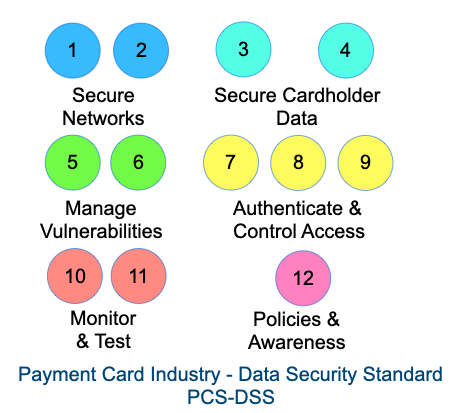
PCI-DSS is broken it up into 12 different modules and this can be reduced to six subsections.
Secure Networks: Build and Maintain a Secure Network and Systems
1. Install and maintain a firewall configuration to protect cardholder data
2. Do not use vendor-supplied defaults for system passwords and other security parameters
Secure Cardholder Data: Protect Cardholder Data
3. Protect stored cardholder data
4. Encrypt transmission of cardholder data across open, public networks
Manage Vulnerabilities: Maintain a Vulnerability Management Program
5. Protect all systems against malware and regularly update antivirus software or programs
6. Develop and maintain secure systems and applications
Authenticate & Control Access: Implement Strong Access Control Measures
7. Restrict access to cardholder data by business need to know
8. Identify and authenticate access to system components
9. Restrict physical access to cardholder data
Monitor and Test: Regularly Monitor and Test Networks
10. Track and monitor all access to network resources and cardholder data
11. Regularly test security systems and processes
Policies and Awareness: Maintain an Information Security Policy
12. Maintain a policy that addresses information security for all personnel
The title of section PCI-DSS section 12 sates it is about policies, but awareness training requirements are also in that section. That is, cybersecurity awareness training for staff. How can someone identify if an email is a valid email or a phishing email? What kind of phishing emails there are?
What other kind of behaviors that might be encouraged or discouraged for during business hours, or even at home.
A good training program is not very intrusive. Typically, 45 minutes to an hour one time for the year and then periodically after that for just a couple of minutes at a time.
Now you are aware of the various frameworks that we modeled this process on, the next step is a risk analysis.
We want to say OK, so where is the data? Where is it being saved? How long is it being saved? Do you have a data retention policy? This is where you delete data after a certain period of time.
All this information combines to give you an exposure profile. Which tells you where you might have some vulnerabilities. Is that data you know susceptible to loss?
What if something happens at Microsoft: They do an update and it goes out for a couple of hours and it comes back and your data is missing. It was not malicious, but you still lost some data. Microsoft and Google don’t guarantee that they will have your data, all they guarantee is that they will provide you the services.
Are you preventing information leaks.? Are you checking to see that the emails are not carrying passport numbers or credit card numbers?
What happens if you are exposed to ransomware? Your server gets locked up, do you have a backup that is isolated from the server?
Do you have that data backed up somewhere offsite? Is it you know up in the cloud somewhere that you can come back, wipe out the server and restore the data? What’s the time gap between backups? How long will it take to restore the data?
These are the things you are Going to be looking at. The output of this is something that’s called a risk register. And the first part of the risk register is that you’re is determining the probability of the identified risk happening. Then, what’s the severity of impact that should that risk happen.
For example:
- Your email system goes unavailable. It does not happen often, and it’s a very low impact because it is Microsoft 365, you have a backup service, and all messages get delivered eventually. So, your score it appropriately and it may be yellow or even green.
- You have a single server just holding all your data and you don’t have a backup on it and it’s all of your client data. There’s a high probability of a single computer having a fault and crashing is relatively high. Losing all your all or a lot of your client data would be a large impact. This would score high on both axis and probably end in the red zone.
You build out the register this way. I had used an example scoring of 1 to 3, but the more granularity you can provide the better you can identify the top risks.
The Risk Register should be more than just a summary of what risks you have. You will want to assign who’s going to be responsible for taking on this task of mitigating each risk.
The risk register is really a good way to actually map out where you are today and it highlights what you need to work on next.
Now that you’ve analyzed everything and you know where you’re at, you enter the Definition phase. Itis time to create your policies.
The first policy you need is an umbrella document, which is normally referred to as the written information security policy (WISP). This will set up the overall scope and key definitions, very high level.
All of your other policies will branch from the WISP.
The purpose for all of your policies, are to provide the definitions, architectures, and responsibilities within the scope of what those policy cover. Policies can enumerate what is allowed, what’s not allowed and what’s restricted.
It is important that everyone in the organization should acknowledge that they’ve received and read these policies. Otherwise, they’re just documents.
Back to the zoom “I’m not a cat” incident; if you had a Computer Use policy that said, the computer is for business use only. The assistant would have known that the daughter couldn’t use the computer and he wouldn’t have had that embarrassing little thing of being a cat.
An option might be to leverage access controls, your policy could say you do allow non staff people to use the computers but they need to use a guest account on the computer. The guest account can be restricted to web access without administrative capabilities, so that malware is much less likely to be able to get installed on it.
A policy may address email. Do you want to restrict email from private use? The policy would let staff know that any email within the business can be read by the owner of the business because it is business property. It is like any other business documentation.
There should be a policy to address passwords. In the past, frequently changing their password was considered a good thing. The problem with that is people run through password burn out and they start to choose less and less strong passwords. Maintaining many strong passwords is one reason for using a password manager, but many businesses are not using one consistently.
Another thing that’s mitigated the frequent changing of passwords is multi factor authentication, commonly every 4-6 months. With MFA you have a username & password and then you have some alternate path of verification. It might be a text message or an acknowledgement email back to you with the code, or it might be an authenticator app.
Microsoft has an authenticator app, Google has one, there’s at least half dozen more authenticator apps out there. With strong unique passwords and MFA, the current recommendation is to you never change the password unless a breach has occurred. In which case then you want to be as conservative as possible and have everyone change and grow and evolve, change their passwords. But in general, you don’t need to change the passwords if you’re using a multi factor method of authentication.
A policy will include a general description of its purpose a and scope. What issues does the policy address? Who does it apply to?
The next part of a policy would be definitions to ensure everyone understands the terms in proper context. Staff may mean employees and contractors. Devices may mean Desktops. Laptops, tablets and smart phones.
The next part would be the directives. Activities may be explicitly permitted, prohibited and restricted
The final part of a policy would be document revision control. Policies will often be updated and revision control is important to ensure everyone has the current version.
Once your policies are in place you move from the definition phase to enforcement. Procedures are the way to document how you enforce the policies in practice.
- What gets recorded for your audit trail?
- How do you respond to incidents? How do you report an incident? What kind of triage needs to be done? Who gets notified?
- How are backups done? How do you verify backups are good? How do you restore from a backup?
- How do you on board and off board staff? How do you track assets?
You do not need to create everything from scratch. There are document templates and many tools whose use will be documented within both the policies and the procedures.
Some of those tools you may already be aware of, and even use them now:
- Advanced endpoint protection includes antivirus and malware detection with profiling and the ability to enforce updates are applied
- Email filtering to reduce SPAM and malware. You can also limit data leaks with outbound filtering.
- Encrypted messaging is important if you frequently deal in sensitive information with your clients.
- Password managers
- SaaS backup protection. Cloud services need backup protection the same a on premise servers.
- Awareness training for staff training is important. Expanding on what I wrote earlier, you can actually gamify it. Who’s got the best score this month? But more importantly you can see how well the business itself is moving up in cyber awareness maturity.
- Network scanning. If you only have one or two computers and network scan isn’t going to tell you much more than what you might already know by looking at the computers themselves. If you have a dozen or more network devices, network scan will go through and find vulnerabilities, classify them and let you work on it.
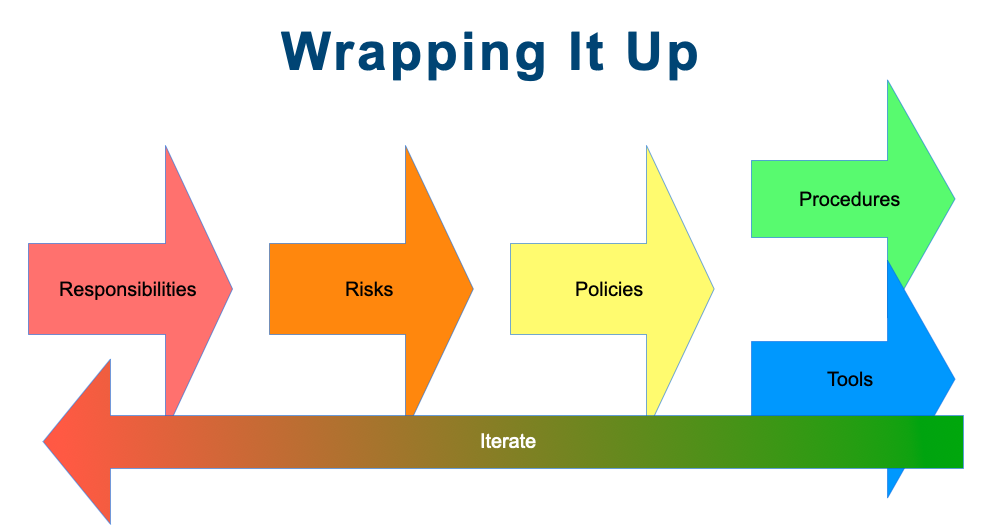
The initial diagram I presented really has a back arrow to indicate that you iterate the process similar to the NIST framework where you have that circular view of things, a constant improvement cycle. As you iterate, you get more and more secure. The goal is first to address the issues that you are required to do, and then the things that you should do, and then the things that you can do.